In the next article, we will review how to use Hestia to create a Joomla business website. But before we do that, we should first explain why we recommend Joomla to build a business website instead of Wordpress. I have previously written an article on the benefits of Joomla over Wordpress which you can read at this link:
https://createyourowninteractivewebsite.com/3-security/3-1-what-is-real-website-security
Given that the security problems of Wordpress websites have been known and well documented for many years, it is amazing that anyone would continue to base their business website on such an insecure web building tool.
The security benefits of Joomla over Wordpress are similar to the security benefits of Linux over Windows. Yet people continue to use Windows to build Wordpress business websites – and then wonder how come their websites were hacked – forcing them to pay millions in Windows and Wordpress ransomware fees. Before we get to the shocking data on Wordpress vulnerabilities, let’s first look at the most recent Windows 10 documented vulnerabilities since the beginning of January 2021 – compared to Linux Debian vulnerabilities during the same period of time.
2021 CVE Windows versus Linux Debian
Linux Debian had 18 reported flaws from January to October 2021.
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=Linux+Debian+2021
These 18 flaws can be broken down into the following root causes:
3- Flatpak (caused by IBM/Redhat)
7 Kernel problems
3 Google Chrome problems
1 Disputed. 1 Avahi problem 1 Intel CPU problem
Thus, so far in 2021, despite upgrading hundreds of packages from Debian 10 to Debian 11, there has not been a single vulnerability reported that was caused by a security error on the part of the Debian team.
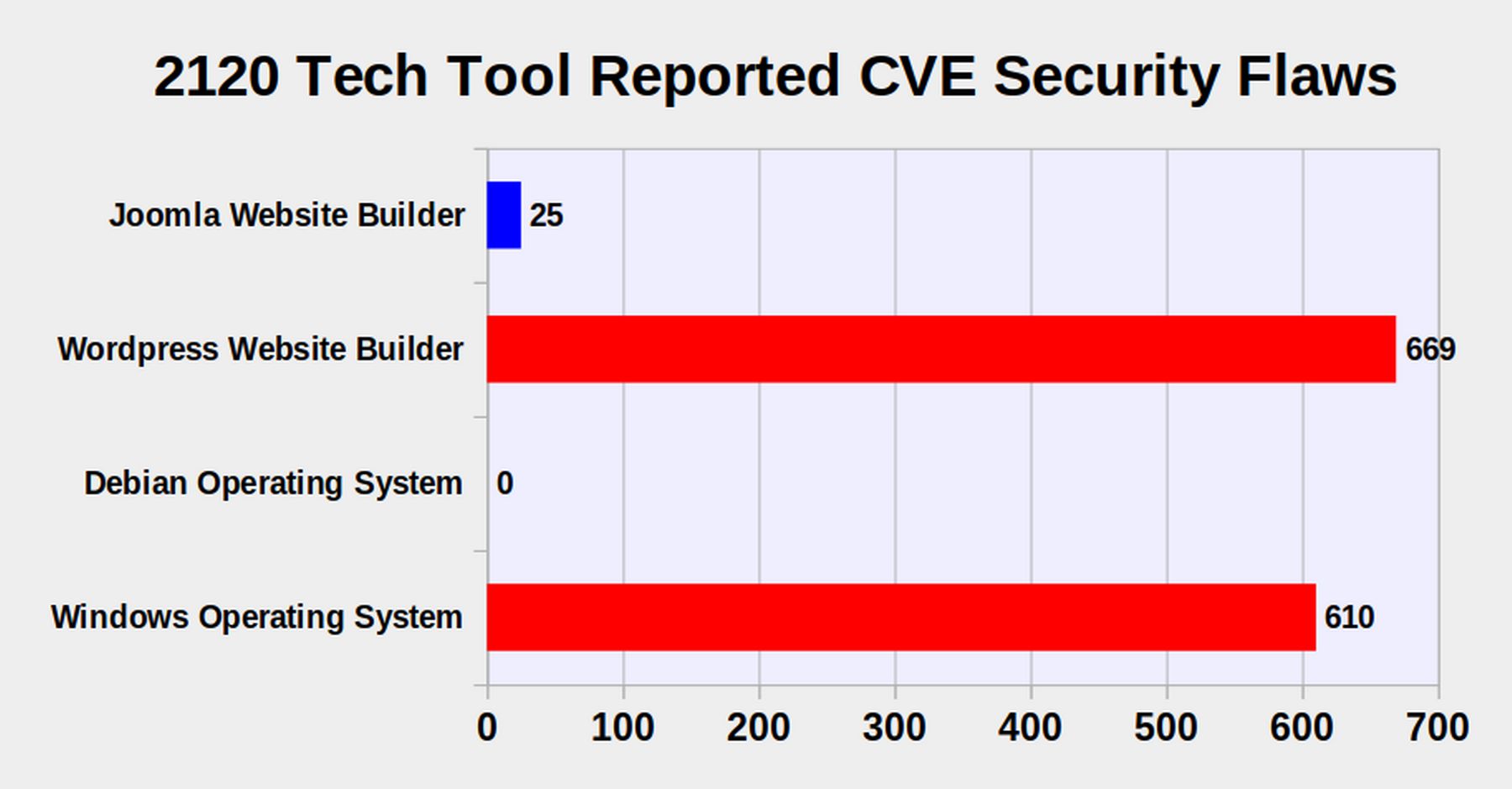
During the past 10 months while the Debian operating system had not a single security error, the Microsoft Windows 10 operating system had 610 Windows security flaws!
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=Windows+2021
The two most common categories of Windows flaws are Remote Code Execution (through the Windows browser) and Elevation of Privilege (because no password is needed for many Windows functions). There are hundreds of examples in both categories.
Every month, more of these Windows flaws are reported. For example, in October 2021, 75 Windows flaws were reported. Microsoft issues “patches” for these flaws. But because the patches do not address the underlying problems in the Windows operating system, each month brings new reports using the same old backdoors.
The question then is this: Why would anyone use the extremely insecure Windows operating system when they could instead use the extremely secure Debian operating system?
Now that we see how ridiculously bad Windows is, let’s look at Wordpress. Here is a real shocker: Wordpress actually has MORE security holes than Windows!
2021 Wordpress CVE versus Joomla
During the first 10 months of 2021, Windows had 610 reported security flaws – while Wordpress had 699! Comparing Wordpress to Joomla, Wordpress had 669 security flaws this year while Joomla has only had 25 flaws so far in 2021. Here is the link:
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=2021+Wordpress
Below is one page out of 30 pages of Wordpress errors this year.
|
Name |
Description |
|---|---|
|
The Leaky Paywall WordPress plugin is vulnerable to Stored Cross-Site Scripting |
|
|
The Content Staging WordPress plugin is vulnerable to Stored Cross-Site Scripting due to insufficient input validation |
|
|
The Indeed Job Importer WordPress plugin is vulnerable to Stored Cross-Site Scripting |
|
|
The Easy Digital Downloads WordPress plugin is vulnerable to Reflected Cross-Site Scripting |
|
|
The Catch Themes Demo Import WordPress plugin is vulnerable to arbitrary file uploads makes it possible for an attacker with administrative privileges to upload malicious files that can be used to achieve remote code execution. |
|
|
The WP Bannerize WordPress plugin is vulnerable to authenticated SQL injection which allows attackers to exfiltrate sensitive information from vulnerable sites. |
|
|
The FV Flowplayer Video Player WordPress plugin is vulnerable to Reflected Cross-Site Scripting |
|
|
The Author Bio Box WordPress plugin is vulnerable to Stored Cross-Site Scripting |
|
|
The LearnPress WordPress plugin is vulnerable to Stored Cross-Site Scripting |
|
|
The Stripe for WooCommerce WordPress plugin is missing a capability check on the save() function makes it possible for attackers to use other site users unique STRIPE identifier and make purchases with their payment accounts. |
|
|
The HAL WordPress plugin is vulnerable to Stored Cross-Site Scripting |
|
|
The KJM Admin Notices WordPress plugin is vulnerable to Stored Cross-Site Scripting |
|
|
The MPL-Publisher WordPress plugin is vulnerable to Stored Cross-Site Scripting |
|
|
The Credova_Financial WordPress plugin discloses a site's associated Credova API account username and password in plaintext |
|
|
The Telefication WordPress plugin is vulnerable to Open Proxy and Server-Side Request Forgery |
|
|
The MyBB Cross-Poster WordPress plugin is vulnerable to Stored Cross-Site Scripting |
|
|
The job-portal WordPress plugin is vulnerable to Stored Cross-Site Scripting |
Here is a summary of the 25 Joomla errors this year (all 25 have been fixed)
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=2021+Joomla
|
Name |
Description |
|---|---|
|
Joomla! 4.0.0. The media manager does not correctly check the user's permissions before executing a file deletion command. |
|
|
Inadequate escaping in the imagelist view of com_media leads to a XSS vulnerability. |
|
|
Install action in com_installer lack the required hardcoded ACL checks for superusers. A default system is not affected |
|
|
CMS functions did not properly termine existing user sessions when a user's password was changed or the user was blocked. |
|
|
Missing validation could lead to a broken usergroups table. |
|
|
Inadequate escaping of the JForm leads to a XSS vulnerability. |
|
|
A missing token check causes a CSRF vulnerability in data download endpoints in com_banners and com_sysinfo. |
|
|
A missing token check causes a CSRF vulnerability in the AJAX reordering endpoint. |
|
|
HTML was missing in the executable block list of MediaHelper::canUpload, leading to XSS attack vectors. |
|
|
Inadequate filters on module layout settings could lead to LFI. |
|
|
Inadequate escaping allowed XSS attacks using the logo parameter of the default templates on error page |
|
|
Inadequate filtering of form contents could allow to overwrite the author field. |
|
|
Extracting a crafted zip package could write files outside of the intended path. |
|
|
Incorrect ACL checks could allow unauthorized change of the category for an article. |
|
|
com_media allowed paths that are not intended for image uploads |
|
|
Missing input validation within the template manager. |
|
|
Missing filtering of feed fields could lead to xss issues. |
|
|
Missing filtering of messages to users could lead to xss issues. |
|
|
The core shipped but unused randval implementation within FOF used a potential insecure implemetation. |
|
|
insufficient length for the 2FA secret of 10 bytes vs 20 bytes. |
|
|
Usage of the insecure rand() function within the process of generating the 2FA secret. |
|
|
The lack of escaping of image-related parameters in multiple com_tags views could lead to XSS attack vectors. |
|
|
The lack of escaping in mod_breadcrumbs aria-label attribute allows XSS attacks. |
|
|
The lack of ACL checks in the orderPosition endpoint of com_modules leak names of unpublished modules. |
Why are Debian and Joomla so much more secure than Windows and Wordpress?
The problems with both Windows and Wordpress is that they are top down corporations controlled by an extremely small group of people whose goals are to maximize short term profits. In the case of Wordpress, all major decisions are made by just a single person. In the case of Microsoft, most of the really bad decisions were made by a guy named Bill Gates many years ago. Microsoft staff and customers have been paying a huge price for his mistakes ever since.
By contrast, Debian and Joomla both consist of a large group of actually users. These users have a vested interested in making sure that the tools they use and create are as secure as possible from hacking attacks. To improve security, both groups have put in place a series of Checks and Balances. These checks and balances slow down innovation a little bit. But they result in a much more secure system in the long run.
Put another way, both Microsoft and Wordpress use very poor coding practices that result in their computers and websites being a bloated mess over time. Just look at any Wordpress website that is more than a few years old. You will see hundreds of articles all on the same page – making it impossible to find the article you are actually looking for. Similarly, after a few years of Windows updates, Windows computers get so bogged down that they literally come to a stop – even if they are not hacked.
Because Debian and Joomla use better structured coding practices, they are like having a clean house – where there are fewer places for hackers to hide.
Now that we have a clearer idea of why we recommend Joomla over Wordpress and Debian over Windows, let’s look at how easy it is to install Joomla on a Debian server using the Hestia Control Panel.

