I grew up out in the country where we have a saying: Never put all your eggs in the same basket. It only takes one mistake on the part of a website administrator to allow hackers into the back end of their website. Almost any Wordpress website can be easily hacked. But even a Joomla website can be hacked if you let your guard down. In this article, we will explain how you can limit the damage done to your websites by using website sub-domains and creating a unique user account for each website.
Examples of how a hacker might access a Joomla website
Here are just a few examples of how a Joomla website might be hacked:
#1 You install a new extension that is badly written and it has security holes that allow hackers to access your website file system. This is particularly a problem with extensions that use a lot of out-dated Javascript libraries.
#2 You allow an employee or volunteer administrator access to the back end of your business website and the employee uses an easily hackable password such as password1. This is what happened to the DNC in 2016 - costing them billions of dollars and the 2016 Presidential Election.
#3 You or an employee or volunteer get lazy and log into your website via an insecure Windows computer at a coffee shop over a WIFI network - thereby giving hackers access to your super administrator log in user name and password.
#4 You have a disgruntled current or former employee who allows administrator access to hackers.
#5 A security update issued while you are on vacation and a hacker gains access.
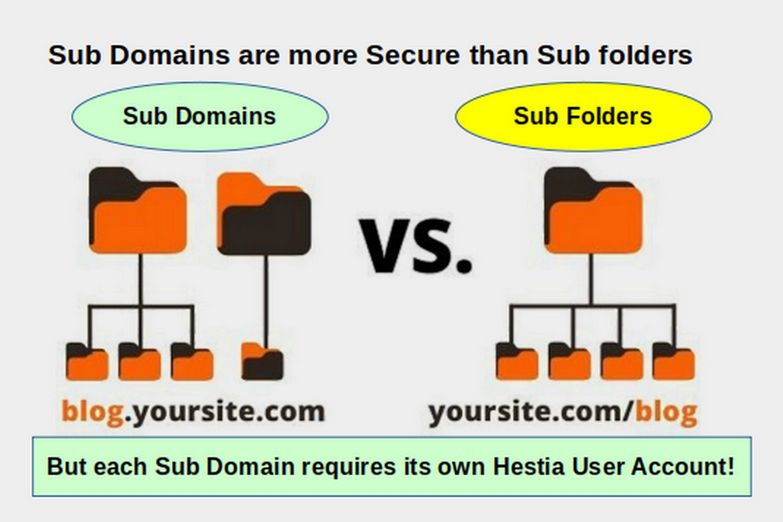
In all of these cases, damage can be limited by using a series of sub-domains and assigning each sub-domain to a unique Hestia User account.
What is a sub domain name?
A sub-domain is an extension of your domain name that comes before your domain name rather than after it. For example, imagine you own the domain name called bestautorepair.com. As your business grows, you add branch stores in several cities such as town1, town2 and town3. It is a common practice to create new pages for each branch so that the home pages for the new branches would be
bestautorepair.com/town1
bestautorepair.com/town2
bestautorepair.com/town3.
Using sub-domains would allow you to create a separate file system for each branch office and the URLs would look like this:
town1.bestautorepair.com
town2.bestautorepair.com
town3.bestautorepair.com
If you then creating a unique Hestia user account for each sub-domain name, hackers who gained access to one branch office website back end would not have access to any other branch office back end. This is assuming that you set each Hestia user account SSH access to the "nologin" setting. Each branch office would have its own file system which is walled off from the file systems of the main website and walled off from the file systems of any other branch office.
Even if you do not have branch offices, you can use sub-domain names to create different Joomla websites for different departments of your store. For example, you can use the sub domain names:
shop.mybusiness.com
services.mybusiness.com
events.mybusiness.com
news.mybusiness.com for website press releases and newsletters
blog.mybusiness.com
docs.mybusiness.com
mail.mybusiness.com
ns1.mybusiness.com (for the name server and Administrator url)
test.mybusiness.com for the development website
support.example.com for the help website
forum.example.com for the public forum for the website
How Hestia Sub Domains compares to Cpanel and WHM
Because Hestia is a free open source control panel, there is no additional cost for additional Hestia Administrator accounts or additional Hestia User Accounts. You can therefore create as many accounts as you need. In my case, I manage over 50 different websites. There are some website designers that manage over 1000 different business website accounts.
Intended mainly for shared hosting companies, Cpanel offers a program called WHM (which stands for Web Host Manager). With this tool, the hosting company can create new Cpanel accounts for each person who buys a new hosting plan from them. Thus, the commercial program WHM is similar to a Hestia Administrator account and each Cpanel account is similar to a Hestia User Account. You can define a package for each Cpanel account in terms of maximum disc space and bandwidth allows, just as you can with a Hestia User account.
But this is where the similarities end. Currently, Cpanel charges $180 per year for an individual Cpanel account - and this price is likely to increase over time. Because Cpanel charges huge fees for Cpanel accounts, businesses have been forced to create all kinds of ways to limit their website hosting costs.
The Danger of Cpanel Secondary or Sub Domain Accounts
One way website owners reduce their Cpanel charges is to by creating secondary or sub-domain website folders in the same file system as their primary website account. How this works is that, similar to Hestia, your primary account is in a folder called public_html. Each secondary or sub-domain account is in a sub-folder in the same public_html folder. For example, the sub-domain website could be called town2.bestautorepair.com.
You then install a separate Joomla application directly in that folder. The actual link to this new website would be bestautorepair.com/town2.bestautorepair. However, this link is forwarded to the sub domain name town2.bestautorepair.com - making it appear to the public like it is a different website when it is actually just a folder inside of the main website folder.
The danger with this structure is that, because the two websites websites are in the same Cpanel public_html folder, any hacker who gains access to any website in this public_html folder has access to ALL of the websites in that same folder. This includes all of the secondary domains and all of the sub domains. I have seen cases where businesses had to rebuild 10 Cpanel managed websites just because one of those websites got breached - and the Cpanel structure allowed the hackers to access all of the other websites without even knowing the passwords for any of those websites.
How Hestia Solves the Secondary and Sub Domain Security Problem
Because Hestia does not charge for individual User Control Panel accounts, you can set up different unique User Accounts for each sub domain name and/or each individual website. In my case, to keep each of my websites walled off from all of my other websites, I had a WHM account that I used to create 50 different Cpanel accounts - one for each of my 50 websites. This was affordable back when Cpanel was virtually free. However the dramatic Cpanel price increase meant that the cost of paying for 50 Cpanel accounts was simply not affordable. Switching these accounts to a VPS with a Hestia Administrator Control Panel and individual user accounts for each website saved me thousands of dollars per year. At the same time, it also meant that each of my website domain names and sub-domain names was much more secure than it had been previously using Cpanel. Therefore the Cpanel price increase was a blessing in disguise - because it forced me to research other Control Panel options.
Managing a Large Number of Hestia User Accounts
The biggest drawback of managing a large number of Hestia User accounts is keeping track of all of the different user names and associated passwords for each website account. This is where a secure Linux password manager can be very helpful.
A Password Manager can suggest and create strong passwords and store them in an encrypted database. You just need to remember the master password for the password manager in order to gain access to each individual website username and password.
Many password managers are online programs. However, a password manager that is located inside of your LMDE computer is more secure than an online password manager. Also some password managers charge for commercial use. Some also charge by the number of users on your password manager account.

An excellent password manager that allows free commercial use and unlimited users is KeepassXC. If you open the LMDE Software Manager, and type keepass into the search box, you will see three password managers all with about the same name:
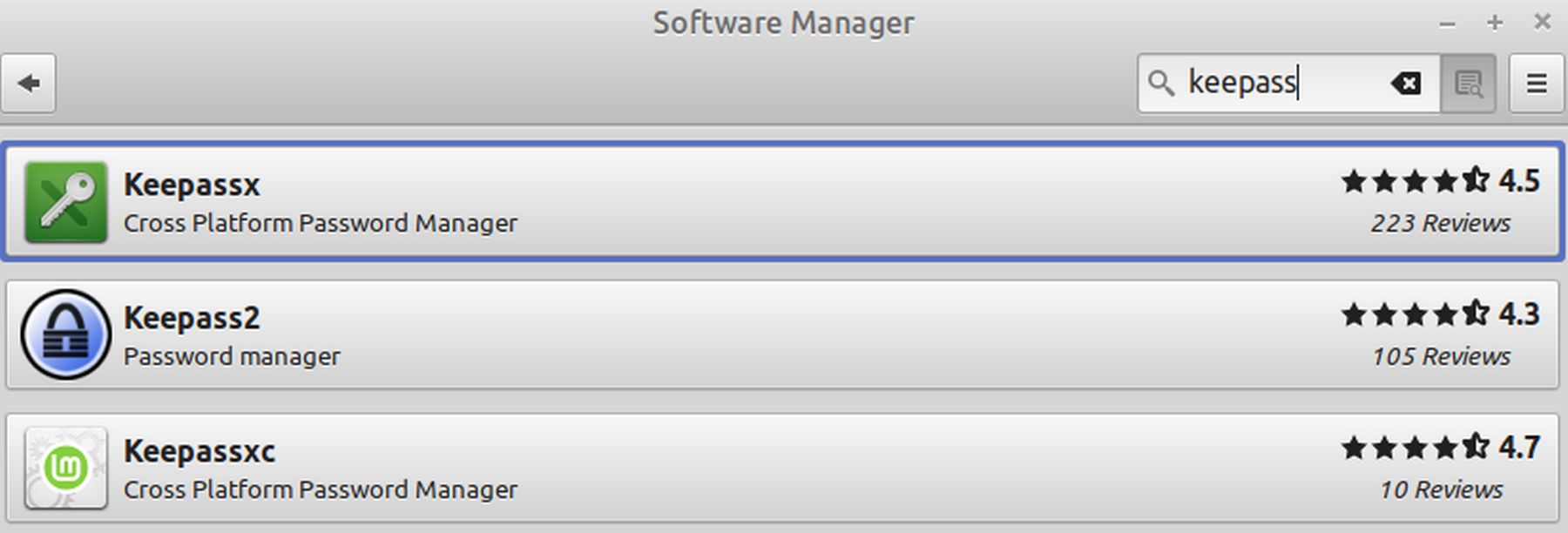
Keepassx has not been maintained in years. Keepass2 is Windows
Keepassxc,m which is what I recommend, is on github
github.com/keepassreboot/keepassxc
The version on the Software Manager is an older version. Therefore you should go to the project Github page to download and install the latest version.
Here are some of the important features:
Browser Integration Available (optional)
Auto-type passwords into applications
Supports exporting to CSV and HTML
YubiKey support
SSH Agent integration available
Folder/Nested Folder support
https://keepassxc.org/download/#linux
Click on the Official AppImage which is a 34 MB File.
They have an excellent Getting Started Guide that will get you up and running quickly. If you need help troubleshooting the browser connection, please read the Setup Browser Integration section.
Looking for more comprehensive documentation? This is found in the User Guide. All major features are documented here including Auto-Type, SSH Agent, and KeeShare
Build and install instructions, and other technical guides, can be found in the Wiki.
https://github.com/keepassxreboot/keepassxc
Also get the Browser integration plugin
https://github.com/keepassxreboot/keepassxc-browser
Click on the latest version button. Then download the Firefox browser zip file.
https://keepassxc.org/docs/KeePassXC_GettingStarted.html#_setup_browser_integration
https://addons.mozilla.org/en-US/firefox/addon/keepassxc-browser/
How to use the Firefox Browser Extension
Find it in https://support.mozilla.org/en-US/questions/1276862:
Create a Keepass entry for Firefox and highlight it in the list
From the menu bar select [Entries->TOTP->Set up TOTP...]
Display the QR code in the FF set up web page and copy to the [Secret Key:] field from above.
Accept defaults and press [OK]
From the menu bar select [Entries->TOTP->Show TOTP..].
copy this number into the response field in the FF set up web page
It should now be all set up.
To use highlight the entry and select [Entries->TOTP->Show TOTP... ](or copy TOTP... if easier)
Why We Should Avoid Cloudflare
Cloudflare is a Content Delivery Network (CDN). It works by caching or storing website content, such as web pages, images and videos, on servers all over the world. The theory is that this will help your web pages load faster as they will load from a server close the person visting your website rather than a distant server – regardless of the location of the server that is actually hosting your website and/or domain name.
However, there are several problems with using Cloudflare. First is the price. While Cloudflare claims to be free, if you want important security features like Website Application Firewall (WAF), Distributed Denial of Service (DDOS) protection and custom SSL, you need their Business Plan, which costs $200 per month. This converts to $2400 per year.
But even if you have a major business and can afford an extra $2400 per year, there are other important reasons to avoid Cloudflare. The biggest reason is that real website security requires true decentralization. Cloudflare, like Microsoft and Google is a top-down monopoly. This makes it much easier and more rewarding for focused hacker attacks. Recent hacker attacks have brought down major corporations including the online store platform Shopify which hosts more than one million businesses. But sadly, makes all of them dependent on Cloudflare. When Cloudflare goes down, all of the websites that depend on Cloudflare also go down. The best way to avoid this problem is to use decentralization.
On May 10, 2021, shortly after the US Pipeline hacker attack, David Kennedy, a former NSA hacker stated: “A lot of these companies, the only result they have is to pay the ransom to recover their entire business. These are big businesses. We’re talking hundreds of millions of dollars, billions of dollars of companies that are impacted by ransomware. It is out of control. Not just DarkSide, but all these other ransomware groups are making hundreds of millions of dollars a year off of ransomware – and there is no sign of any slowdown. In fact, we’ve seen a 300% increase this year alone in ransomware activity.”
https://www.cnbc.com/2021/05/10/cloudflare-ceo-on-uptick-in-cyber-incidents-colonial-pipeline-attack.html
Even if you can afford a $5 million blackmail fee to get your business back, there are other reasons to avoid Cloudflare. Several case studies of major corporations have shown that Cloudflare can result in a dramatic drop in Search Engine Rankings (commonly called SEO). Here is an image of traffic to one major business website confirming that disabling Cloudflare immediately increased their website traffic:
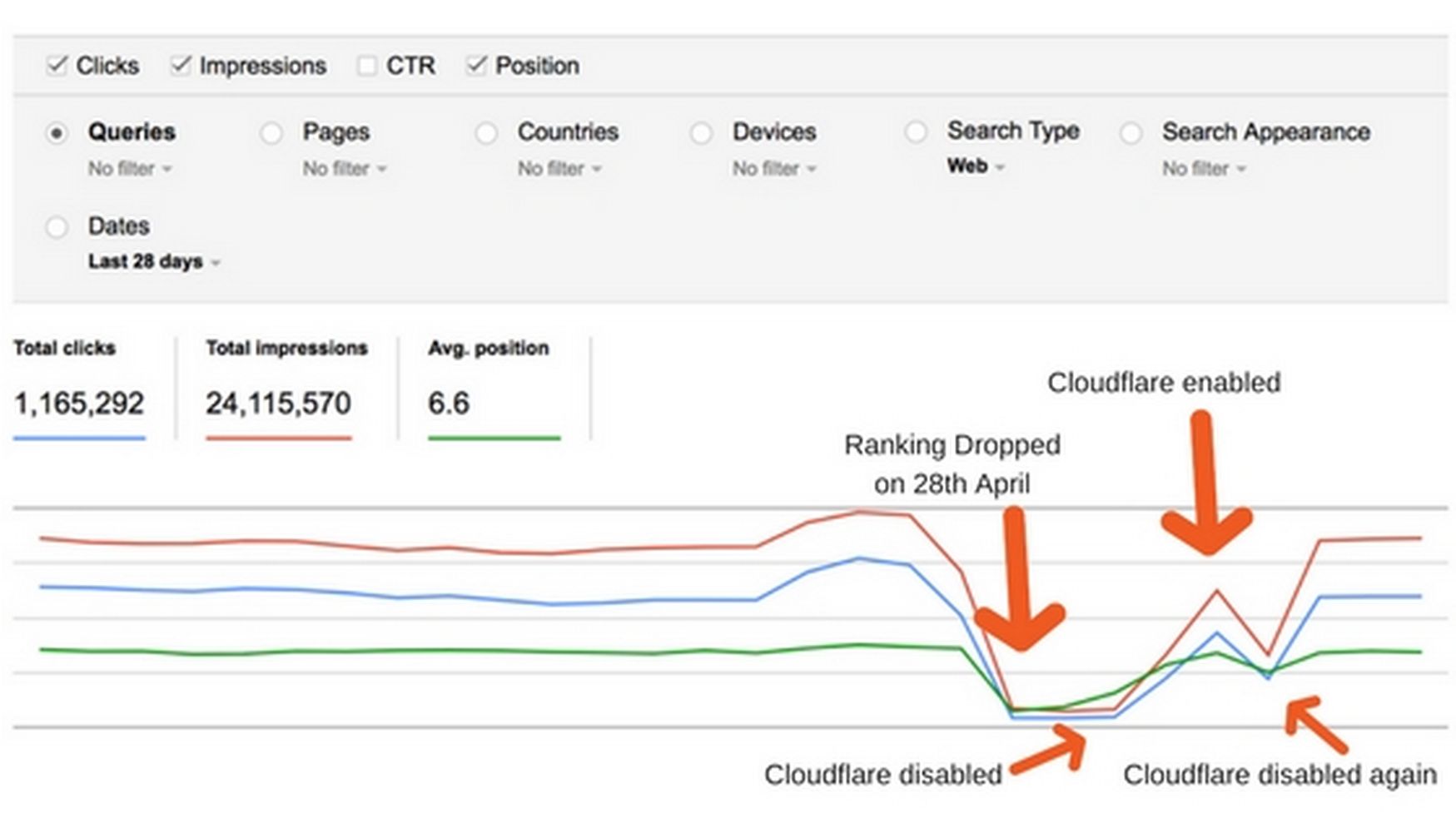
Many people have noticed that their sites lost traffic after enabling Cloudflare. Here is a link to a major business that tried out Cloudflare and saw their website visits immediately drop from 50 to 500 visits per day down to 0 to 7 visits per day basically because their Search Engine rankings fell from #2 (top of the first page) to no ranking at all (not on the first 10 pages). When the business switched back to their original name servers, their search engine ranking and web traffic was restored within 24 hours.
https://www.reddit.com/r/bigseo/comments/3htcot/cloudflare_rankings_destroyed_in_36_hours/
Best Alternatives to Cloudflare
The following analysis of a similar Cloudflare traffic drop correctly concluded that the problem was due to using a Cloudflare shared IP address. Here is a quote from the analysis:
So what actually happens when you enable CloudFlare? Your site is no longer served from its original IP, that is, the IP of your server. But it is going to have the shared IP of the proxy server i.e. Cloudflare. The Cloudflare IP will change depending on the geolocation of the requesting client. This means, Cloudflare basically becomes your DNS. Your site will share those IPs with many other sites using the Cloudflare service. Those sites could be big enterprises or a spammer or malware, distributor.”
https://serverguy.com/case-study/cloudflare-seo/
The solution to this problem is to create a dedicated Virtual Private Server on a reputable web host which is using a dedicated IP address that is not shared with anyone.
Hestia Offers Two DNS Options
Hestia is somewhat compatible with Cloudflare. But wisely, they do not recommend Cloudflare and instead offer two much better alternatives. The Hestia preferred alternative, widely discussed on their forum is to set up two virtual private servers (each with its own IP address and each with its own Hestia Installation). One of the servers is used for web hosting and the other server is used for a DNS and Mail Server.
While this is the most secure arrangement, there are some problems with this two server solution. The first problem is that it doubles the cost as you need to pay a Cloud VPS Hosting company for two servers instead of one. If using the Fullhost Cloud VPS, this means $60 per month instead of $30 per month.
The second problem is that you need to learn how to install and maintain your own DNS server. Hestia makes this process relatively easy. But setting up your own BIND DNS server can be challenging. My advice is to use training tools like VMM to learn how to complete the needed steps. There are free (and long) PDF manuals online this process.
Because it would take more than 100 pages to properly describe this BIND DNS Server set up process, we will cover a simple and more direct process which is only slightly less secure. The process I recommend involves only using one cloud server to host your websites and custom email service – and then using a domain name registrar (aka Canhost) to host the DNS server. This is the process we described in detail in our previous articles.
The chief benefit of using Canhost for both Domain Registration and DNS Management is that if there is ever a DNS problem, Canhost is has all of the needed tools to help you solve the problem. To me, it just makes sense to have all of the DNS Management in the same place and under the control of people who really know what they are doing. This leaves you free to do what matters most to you – which should be managing the content on your business website.
What's Next?
This completes our chapter on data security. In the next chapter, we will review some important Hestia VPS administration tools including how to set up custom business email accounts and how to set up a backup system.

